
This is an extension of the Fork DRMConnector.
Single machine (B) running the OMII container with the GridSAM Web Service deployed. Jobs are launched on the execution machine (C). OMII container (B) is available to the Internet. User holding a certificate trusted by the OMII container (B) can submit jobs over the internet to the GridSAM instance running on the OMII container (B). Host (C) provides SSH and SFTP access to an identity used by (B), therefore GridSAM hosted on (B) can launch jobs and stage files onto the execution host securely under a DIFFERENT IDENTITY to the user operating the OMII container.
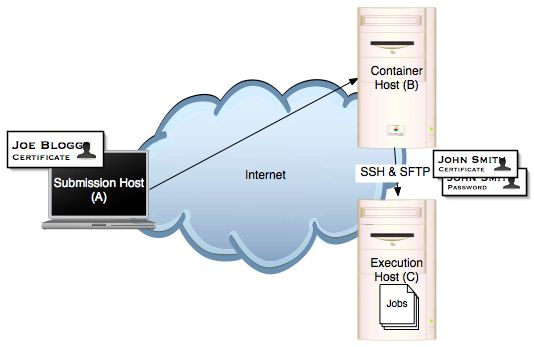
There must be a working Secure Shell Server running on host C. The user running the OMII container must be able to login to the SSH server using username/password or public key authentication.
<?xml version="1.0" encoding="UTF-8"?>
<module id="jobmanager.ssh" version="1.0.0">
<!-- dependent modules -->
<sub-module descriptor="org/icenigrid/gridsam/resource/config/common.xml"/>
<sub-module descriptor="org/icenigrid/gridsam/resource/config/embedded.xml"/>
<sub-module descriptor="org/icenigrid/gridsam/resource/config/fork.xml"/>
<sub-module descriptor="org/icenigrid/gridsam/resource/config/shell.xml"/>
<sub-module descriptor="org/icenigrid/gridsam/resource/config/ssh.xml"/>
<sub-module descriptor="database.xml"/>
<sub-module descriptor="authorisation.xml"/>
<!-- override the factory defaults here -->
<contribution configuration-id="hivemind.ApplicationDefaults">
<!--
The spooling directory for shell-based job submission
-->
<default symbol="spool.directory" value="/tmp"/>
</contribution>
<!-- SSH shell configuration -->
<!-- modify the following contribution to reflect your SSH execution host -->
<contribution configuration-id="ssh.ShellConfig">
<Server host="localhost" user="${user.name}">
<PublicKeyAuthentication keyfile="${user.home}/.ssh/id_rsa" passphrase=""/>
<!-- or
<PasswordAuthentication password="$[password to access (C)]" />
-->
</Server>
</contribution>
</module><Server host="[hostname of (C)]" user="[username to connect as]">
<PublicKeyAuthentication
keyfile="$[RSA keyfile for public key authentication]"
passphrase="${passphrase for unlocking the keyfile}"? /> |
<PasswordAuthentication password="$[password to access (C)]" />
</Server>GridSAM provides Public-Key and Username/Password authentication to the execution host. You can find more information on Public-Key authentication here.
Jobs can be executed remotely to the host running the OMII container. Also, the job can be executed under a different user. Administrator of the execution host can provide a restricted account on host (C) for execution only. However, all jobs are run under the account chosen by (B), therefore potentially there can still be interference between jobs. Also hosts (B) and (C) can be the same host therefore providing a similar scenario to Local Forking, however jobs can be executed under a different account to the one used to launch the OMII container. Te nature of SSH allows secure job launching over a wide area network, therefore the OMII container and the execution host can be widely distributed.